Embrace your best security asset: Your Team
Your team is your best defense against attacks. Empower them to build safe, scalable access workflows.

Remove the risk of over-provisioned access
Automatically grant or revoke access to your production environment to help maintain Zero Trust.
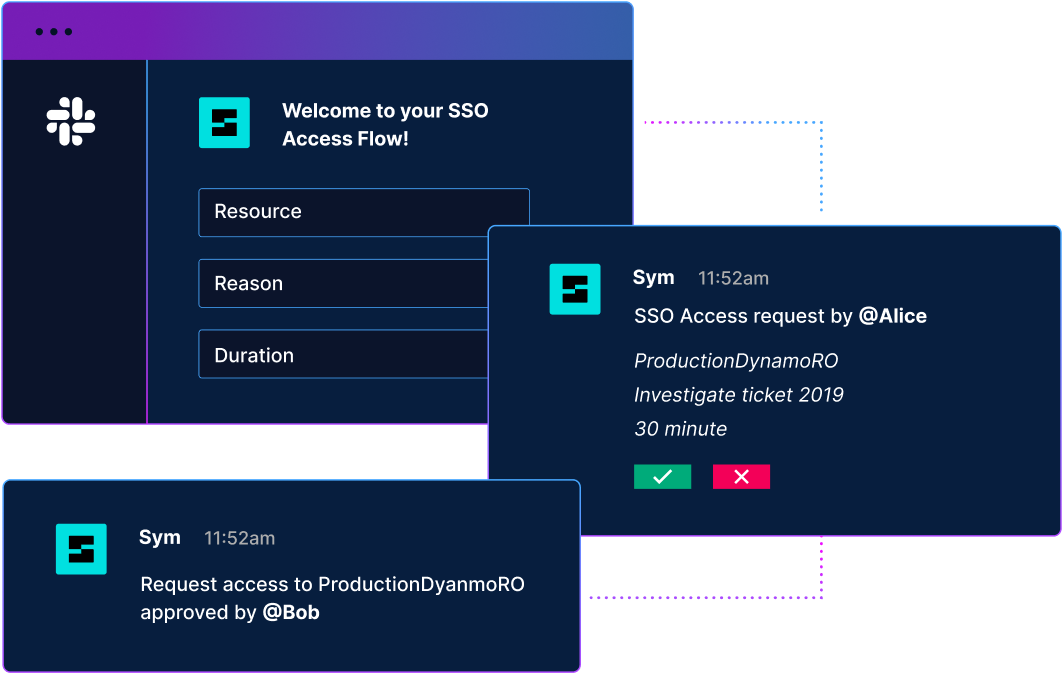
Replace manual ticket queues
Send access requests to the right approver automatically. Automate predictable access request patterns to avoid bottlenecks.
Boost visibility and collaboration
Access a complete record of who was granted access to what. Help mitigate risk & fulfill compliance like SOC 2.
Bryter
Joao Martins
Product Security Manager
Symops has been a game-changer for BRYTER, helping us mitigate risks from uncontrolled and open-ended access into AWS. We’ve eliminated bottlenecks and streamlined our workflows while maintaining a clear audit trail.
Simplify access management
Read the guide on implementing Zero Trust Security
Practical advice for improving your security posture with zero trust.
Reduce friction. Unblock your engineers.
Sym's SDK helps platform, security and infrastructure teams build authorization flows with the tools that they love. All with centralized governance using your organization's SDLC.
